Generally Firefox as a product is not the problem, the Mozilla Foundation is. When you tweak Firefox you not only run with the latest version of Firefox, but you also get a true privacy-respecting browser. Firefox is unique in this way as no other browser, as far as I know, allows for so much tweaking without patching. Because you probably won’t ever need to use a Captive Portal on your pentesting machine (a VM, in my case), you can completely disable Firefox’s attempts to detect them. Just browse to about:config and enter network.captive-portal-service.enabled. Double click it to change its value to “false” and you should be good to go. Captive Portal feature covers the detection and implementation of handles for captive portals inside Firefox browser. Firefox is expected to handle the handling of a captive portal page upon detection of such.
Hi Support,In our environment we have many hundreds of clients/visitors that heavily use the web.
Needless to say that Firefox is one of the most used web clients.
We noticed a continuous hit on our firewalls which took it's toll on the cpus as the request to hhttp://detectportal.firefox.com/success.txt is from every Firefox browser installed on the desktops/laptops/etc every 3 seconds or so.
As a workaround we've allowed through the firewall an ever growing list of IP addresses and that is plain ridiculous and simply unmanageable.
Are your network gurus/engineers going to implement solutions such as anycast to alleviate this flawed implementation of a simple service as it has been in use for quite sometime now by for example Apple, Google, etc...
For example if you ping 8.8.8.8, it's very likely hosted in a datacentre near your town.
Will you consider anycast towards detectportal.firefox.com?
Please advise.
Thanks in advance.
Yves
Published on 2020-10-20. Updated on 2020-10-26
Privacy on the Internet is important because privacy risks range from the gathering of statistics on users to more malicious acts such as the spreading of spyware and the exploitation of various forms of bugs (software faults). Many companies, such as Google, track which websites people visit and then use the information, for instance by sending advertising based on one's web browsing history. Sometimes prices on products are changed on the same website, depending on tracking information, and two people may view the exact same product on the exact same website yet be presented with very different prices.
Table of contents
- Privacy compromising browsers
- Tweaking Firefox - the best solution
Introduction
This article isn't specifically about privacy issues only, it's about promises that are being broken, which might be about privacy. It is also about the lack of user freedom, as in the choice to enable or disable features, such as automatic updates, or forced usage of third party services, or software that the user generally is unaware of or don't have a say about.
Privacy as a subject regarding the usage of services on the Internet is a very difficult subject to deal with. Not only can it be difficult to actually define privacy, but it also requires a balance between freedom of choice by the users, security and usability. Naturally you need to be able to use the browser on the Internet and as such you will always leave some kind of trail behind, and this article is not about how you can hide your tracks. What I am addressing in this article are browsers that are either promoted as 'privacy-respecting' by the developers, or in general are considered to be so (mostly due to misunderstanding or misinformation), while it is very clear they are not.
Some browsers either directly violate users by collecting telemetric data without consent, or you have to opt-out rather than opt-in, or they bounce around the Internet visiting places in the background without you knowing (using dns-prefetch or automatic updates etc.), using third party services that operates with a privacy policy you either cannot trust, or that are directly violating your privacy, or they have integrated third party software that do some of these things.
I will try to keep this article updated with relevant information as much as possible. I know several other browsers exist, but if they are not mentioned on this list I have either not had a change to investigate them, they are closed source and completely irrelevant (such as Microsoft Edge or Opera), or they are not actively maintained, or they cannot perhaps be trusted for some reason or another.
I will also not be looking at browsers that only work on Microsoft Windows or macOS, even if they are Open Source. Both Microsoft Windows and macOS are highly controversial and completely untrustworthy operating systems.
Also please note that just because the developers of a browser are promising that their browser is privacy-respecting doesn't mean that you can trust the information. As you will see with the examples of some of the browsers below even developers some times compromise user privacy perhaps without even thinking about it.
I also want to make a strong advice to people recommending browsers to other people without investigation or knowledge. The privacy related channel on Reddit is filled with wrong recommendations regarding privacy-respecting browsers and many people are merely guessing or blindly trusting the information the browser producers are publishing. Neither Mozilla Firefox, Google Chrome or Chromium, Brave, Waterfox, or several of the other recommended browsers truly respect privacy. They all do some form of telemetry and/or privacy-compromising actions without the user consenting to it or even knowing about it.
Also, privacy doesn't mean that you simply pull out telemetry from Firefox, rebrand it, and then ship it. Privacy is more than that. Unless the browser is automatically checking for an updated version, and the website isn't logging that request, it cannot be considered truly private if the browser starts bouncing around on the Internet visiting all kinds of places without the user has done anything more than open the browser up! Every time the browser makes a DNS request, that DNS request is in most cases logged unless the user actively does something to mitigate that - such as using a trusted VPN or non-logging DNS service etc. Furthermore, the Mozilla add-on CDN is logging user activity, as is Amazon Cloudfront, so if the browser visits these places without the user explicitly pushes a 'check for updates' option, the browser is compromising user privacy. The point I'm trying to make is that the user needs to have the choice and that nothing happens until the user actively do something.
Last, but not least, if you discover any mistakes on my part, feel free to email me about it so that I can correct the information.
Privacy compromising browsers
Mozilla Firefox
In the past I have always supported Mozilla and promoted Firefox, but Mozilla has made some pretty controversial decisions as of late and I no longer feel that Mozilla is an organization that deserves any support. Not unless they change the way they conduct their business.
Firefox is promoted by Mozilla as a privacy-respecting browser, but this is highly misleading. Firefox 'phones home' every time you start it up even when you have disabled telemetry and automatic updates of extensions. Domains such as mozilla.org, cloudfront.net, firefox.settings.services.mozilla.com (see: https://bugzilla.mozilla.org/show_bug.cgi?id=1598562#c12), autopush.prod.mozaws.net, detectportal.firefox.com and location.services.mozilla.com are visited each time you start Firefox.
In 2017 Mozilla made a deal with Cliqz where approximately 1% of users downloading Firefox in Germany would receive a version with Cliqz software included. And in 2018 Mozilla revealed that they had no data on the number of Firefox installations with disabled Telemetry.
Mozilla then developed the Telemetry Coverage system and distributed it to 1% of the Firefox installations. The system is automatically installed and designed to inform Mozilla whether telemetry is enabled in the browser.
Mozilla also developed a Windows-only scheduled task which runs in the background once a day for each installation of Firefox installed on a computer running Microsoft Windows. The task collects information related to the system's current and previous default browser setting and the operating system locale and version.
This is a list of some of the things that Mozilla collects: https://www.mozilla.org/en-US/privacy/firefox/#suggest-relevant-content.
On the Mozilla website we can read (when I originally started writing this article) that We put people over profit
, and a product to support user privacy
. We can also read in the Mozilla manifesto, in the fourth principle, that Individuals' security and privacy on the internet are fundamental and must not be treated as optional.
However, with their decision to make Cloudflare the default DNS provider for DNS over HTTPS, they are definitely not supporting user privacy or putting people over profit!
DNS over HTTPS is by itself bad enough, and highly criticized with very good reason, but combining it with a US based company like Cloudflare makes it even worse. Cloudflare cannot be trusted with DNS requests.
Cloudflare has made an agreement with Mozilla that when it acts as a DNS resolver for Firefox, that:
- DNS requests will be stored as part of Cloudflare's 'temporary' logs which are permanently deleted within 24 hours.
- Cloudflare will also collect and store the following information as part of its permanent logs:
- Total number of requests processed by each Cloudflare co-location facility.
- Aggregate list of all domain names requested.
- Samples of domain names queried along with the times of such queries.
- Information stored in Cloudflare's permanent logs will be anonymized and may be held indefinitely by Cloudflare for its own internal research and development purposes.
Anyone who has worked with DNS servers knows what goes into such logs and in order for Cloudflare to keep their promise they need to: Delete the DNS requests information, but at the same time somehow still keep 'anonymized' logs of the total number of requests, a list of all domain names requested, a so-called 'sample' of complete DNS queries along with date and time.
This means that even if Cloudflare could be trusted and they have the best of intentions, they will still log everything the first 24 hours. If Cloudflare is ever compromised all these logs could be copied and distributed over a period of time.
Furthermore, the actual wording of the agreement is such that the technical procedure for how they actually do this can only be guessed at. How do they plan to anonymize the data? Is the 'sample' 99.9% of all the queries, or is it 1%?
Last, but not least, Cloudflare is an American company subject to American law, a law that pretty much undermines the foundation of any kind of privacy.
Cloudflare will not retain or sell or transfer to any third party (except as may be required by law) any personal information, IP addresses or other user identifiers from the DNS queries sent from the Firefox browser to the Cloudflare Resolver for Firefox;
Real privacy means:
- No logging
- No data retention
- No phoning home without consent before doing so
- No user opt-out telemetry, it has to be opt-in
- Real and 100% transparency regarding what data is collected
- Absolutely no integration of company based services such as Google Search or Cloudflare DNS
Period!
Mozilla are promoting Firefox as a product to support user privacy and freedom, yet at the same time they make Google the default search engine in the browser because Google pays them and Cloudflare the default DNS over HTTPS resolver.
Update 2020-10-25: Another relevant reading regarding the payment by Google to Mozilla is: US Department Of Justice Lawsuit Against Google Could Kill Firefox.
Firefox in itself has long been submitting data to the Mozilla foundation via its 'Data Collection and Use' gathering. Even though this data is 'technical and interaction data', the data collection is opt-out, meaning that you have to remember to disable it rather than enable it. This also means that the very first time you start up Firefox, it has already connected to the Mozilla foundation before you can disable the data collection. If you forget to disable the data collection and later disable it, you'll get the following information from Firefox: You're no longer allowing Mozilla to capture technical and interaction data. All past data will be deleted within 30 days.
There is no option to delete the data gathering right away.
This is an example of some of the destination addresses a network analysis reveals about some of the DNS and HTTPS requests Firefox makes even when telemetry and automatic updates are completely disabled:
- detectportal.firefox.com
- detectportal.prod.mozaws.net
- detectportal.firefox.com-v2.edgesuite.net
- a1089.dscd.akamai.net
- mozilla.org
- location.services.mozilla.com
- content-signature-2.cdn.mozilla.net
- locprod1-elb-eu-west-1.prod.mozaws.net
- d2nxq2uap88usk.cloudfront.net
- firefox.settings.services.mozilla.com
- push.services.mozilla.com
- ec2-52-35-220-92.us-west-2.compute.amazonaws.com
- ec2-34-242-33-12.eu-west-1.compute.amazonaws.com
- server-13-33-240-52.hel50.r.cloudfront.net
- shavar.services.mozilla.com
The Mozilla Annual Repport is filled with empty promises and contradictory statements:
Our promise is to help make clear that privacy is non-negotiable, and we delivered on this promise in 2018 and 2019 by providing consumers with a range of tools beyond the browser that are built from the ground up to provide security and preserve privacy.
While some of our competitors may be new to the notion of privacy, it has always been at the core of everything we do. Mozilla is secure by default; it always has been, and it always will be.
The pervasive and hidden nature of third-party, cross-site tracking has allowed companies virtually unfettered access to the data generated by people’s online activities. This has enabled micro-targeting and predictive profiles to be built by companies which influence the types of ads, services and information people are presented online. Without the ability to curb this type of data collection, people’s control over their online experiences is severely limited.
Mozilla: this is called double standard.
Of course Mozilla has done a ton of good too, but being the heavily monetized foundation it has become, Mozilla is a business that no longer can survive without funding from major companies such as Google, and as such a major conflict of interest exists.
Other recommended reading regarding Mozilla and Firefox:
Google Chrome and Chromium
Google's Chrome and Chromium browsers are even worse than Firefox. Every time you start Chrome or Chromium the browser contacts Google and almost every key press performed in the browsers address field is submitted as part of the data collection send to Google.
Chrome is worse than Chromium because Chrome contains closed source and it is impossible to know exactly what data is send to Google. In principle Google could be reading all your passwords when you login to a service online. And this goes of course as well for any other closed source browser.
This is an example of some of the destination addresses a network analysis reveals about some of the DNS and HTTPS requests Chromium on Linux makes when it is first started:
- redirector.gvt1.com
- www.google.com
- accounts.google.com
- r1---sn-25g3oxu-j2ie.gvt1.com
- ams15s40-in-f14.1e100.net
- ams15s40-in-f13.1e100.net
- ams16s31-in-f3.1e100.net
- fonts.googleapis.com
- www.gstatic.com
- gstaticadssl.l.google.com
- apis.google.com
- plus.l.google.com
- ogs.google.com
- www3.l.google.com
I will not address many of the specific Chrome/Chromium related privacy problems as Google has become very famous for their privacy-compromising policies regarding all their products and services. They at least openly proclaim that they monitor every step you take and they do not hide that fact.
On the Google Privacy & Terms page we can clearly read: We collect information to provide better services to all our users — from figuring out basic stuff like which language you speak, to more complex things like which ads you'll find most useful, the people who matter most to you online, or which YouTube videos you might like.
and When you're not signed in to a Google Account, we store the information we collect with unique identifiers tied to the browser, application, or device you're using.
This means that Google is openly trying to fingerprinting you and track your every move, even when you're not logged into a Google account or even using Chrome or Chromium.
Whenever you use any of Googles products or services you automatically forfeit your privacy. If you don't like it, don't use their stuff, they say. However, it is not that simple. Google has managed to sneak their spying software on to almost every website on the Internet and you have to manually and proactively take measures to ensure that Google cannot track you.
Brave
The Brave browser is often recommended by people as a privacy-respecting alternative to both Firefox and Chrome, but this is a mistake. Brave is no better that the alternatives.
People are being mislead by the empty promises of privacy. Brave not only also 'phones home' it also hijacks links and insert affiliate codes, which was found out by Cryptonator1337 on Twitter. Furthermore the 'anonymously monitoring of user attention' and 'rewards publishers accordingly with Basic Attention Token (BAT) crypto currency' is not something that should be recommended.
Another privacy issue that was discovered regarding Brave was that clearing the history doesn't remove 'Top Sites' on the new tab page.
No, the Brave browser is not a privacy-respecting browser.
Palemoon
Palemoon is also sometimes recommended by people as a privacy-respecting browser, but Palemoon is not even promoted as a privacy-respecting browser so I don't know where that comes from. Palemoon also 'phones home' and it also connects to Google every time it is started up just like Chromium.
Waterfox
Waterfox is yet another browser that people sometimes recommend as a privacy-respecting browser, but that is also not correct.
Not only does Waterfox connect to a ton of domains when it is started, such as both Mozilla add-on CDN and Amazon Cloudfront, but it is also clearly stated in the project privacy policy that If our organizational structure or status changes (if we undergo a restructuring, are acquired, or go bankrupt) we may pass your information to a successor.
Furthermore it is stated that If you engage with our social media accounts, such as Twitter and Facebook, we may receive personal information about you. If you use these networks, their privacy policies apply, and you are encouraged to read them.
and We may use cookies, third party web analytics, device information, and IP addresses for functionality and to better understand user interaction with our products, services, and communications.
and We may also use cookies and/or IP addresses, to help us understand in the aggregate how users engage with our products, services, communications, websites, online campaigns and other platforms.
So no, Waterfox is also not a privacy-respecting browser.
Librewolf
Librewolf is promoted as the community-maintained fork of Librefox: a privacy and security-focused browser
however Librewolf is suffering from the same problems as Waterfox.
Librewolf is a set of scripts and patches that removes the Firefox telemetry feature among other things. However, a network dump reveals that the very first time Librewolf is started it immediately contacts the Mozilla add-on CDN, Amazon Cloudfront, and several other places even though automatic updates of extensions is disabled by default.
The network dump reveals some of the following domains and IP addresses (I have shortened the list):
- addons.cdn.mozilla.net
- server-13-33-240-122.hel50.r.cloudfront.net
- ec2-34-253-97-22.eu-west-1.compute.amazonaws.com
- content-signature-2.cdn.mozilla.net
- rt4bb146-89-147.routit.net
- invidio.us
- static.213-133-100-23.clients.your-server.de
- 132.145.233.26
- 52.142.124.215
- 167.99.237.63
- 194.187.168.100
While it is true that the project themselves do not collect any telemetry, the domains that the browser visits the very first time you open up the browser do log these requests.
Librewolf should not be bouncing around on the Internet without the user explicitly asking it to do so.
GNOME Web (formerly Epiphany) and Eolie
GNOME Web is a good example of how complicated and difficult things can really get.
GNOME Web is a web browser from the GNOME project. When you read the information on the website it is stated that by default GNOME Web tries to be privacy-respecting and the project receives no funding from advertisers. The project aim to offer the best out-of-the-box privacy settings of any general purpose web browser. However, they actually fail at this.
A network analysis reveals that GNOME Web contacts the easylist-downloads.adblockplus.org domain the first time it is started up, which I guess is in order to check whether the browser is running with the latest ad blocking filters. On the AdBlock Plus FAQ website it clearly states that AdBlock Plus collects personal information and that this information is used by the company eyeo GmbH (Germany). It is further revealed in the Privacy Policy that quite a lot of personal data is collected.
All the problems related to GNOME Web is also valid for Eolie.
It is problematic that the GNOME project promotes GNOME Web as a privacy-respecting browser yet at the same time integrates an ad blocker from a company that is compromising user privacy. However, I do not believe in any way that this is intentional, I believe that perhaps nobody has thought about this. The best options for both GNOME Web and Eolie is to make the browsers provide a choice between manual updates of the lists and not to do anything before the user has accepted that.
Neither GNOME Web nor Eolie are true privacy-respecting browsers.
Midori Browser
The Midori Browser is an Open Source lightweight web browser that uses the Apple WebKit rendering engine and the GTK2 or GTK3 interface. Midori is part of the Xfce desktop environment and was developed to follow the Xfce principle of making the most out of available resources
. Midori is the default browser in a bunch of Linux distributions.
In 2019, the Midori project was merged with the Astian Foundation and one problematic issue regarding the privacy of Midori is that things may now change without notice. This is, in my humble opinion, a sad and big mistake by the Xfce project.
On the Privacy Policy (in Spanish) the Astian Foundation states that The Astian Group is committed to the security and privacy of its users' data. When we ask you to fill in the fields of personal information with which you can be identified, we do so ensuring that it will only be used in accordance with the terms of this document. However, this Privacy Policy may change over time or be updated, so we recommend and emphasize that you continually review this page to ensure that you agree with said changes.
At the same time the foundation also writes that The content of the website is provided to the public as it appears or as it is available. We do not represent or promise anything with regard to the content of the website including its accuracy, completeness, advice given or statement made through the website or any other future-oriented. Therefore, we do not have any responsibility derived from the use that you or any person makes of the material or content of the website.
which is just another way to disclaim responsibility.
I have not looked through the source code of Midory, but a network analysis reveals that as soon as you enable the ad blocking extension in the Extensions tab a couple of requests are made to Amazon Cloudfront. No matter what this is used for Amazon Cloudfront is logging and compromising user privacy.
Furthermore, I find the privacy policy of the Astian Foundation dubious and see no reason to promote the Midori Browser when better alternatives exists.
Other problematic browsers
The browsers listed below suffers from some of the same problems as the browsers listed above. I will not address all the specific issues I have found on these browsers, but will simply put them on the list.
- vimb (dns-prefetching)
- Iridium Browser (looks abandoned)
Privacy respecting browsers
It is important to note that the browsers listed below, with the exception of the 'Tweaking Firefox section', cannot be considered on the same level of security attention as Firefox or Chromium. This is mainly due to the size and level of support both these browsers get. This however does not automatically mean that the other browsers are less secure. Both Firefox and Chromium, due to the huge size of these browsers, and the large amount of code that goes into these two projects, have a considerably larger attack vector.
No matter what browser you use, you need to keep a very close eye on exploitable bugs and other security issues and it is important to subscribe to mailing lists, news letters, etc., which provide browser related security information in a timely manner.
Even though a security bug might be exploitable it doesn't necessarily mean that it specifically affects your usage of the browser, it all depends on circumstance and usage. Every persons millage varies and if you only need to read the news you can decrease the thread level substantially just by disabling support for JavaScript or use a simple console based browser.
Tweaking Firefox - the best solution
Firefox is one of the most extensible and tweakable browsers in the world, which makes it possible to increase the privacy in Firefox considerably by using different configurations and tweaks without having to patch the source code. And this is one of the things that makes Firefox really great. Generally Firefox as a product is not the problem, the Mozilla Foundation is. When you tweak Firefox you not only run with the latest version of Firefox, but you also get a true privacy-respecting browser.
Firefox is unique in this way as no other browser, as far as I know, allows for so much tweaking without patching. Tweaks are settings that control Firefox's behavior. Some can be set from the options interface, which can be in about:config, but others are called 'hidden preferences' which will only show when they are set by the user.
Tweaking Firefox is not for everyone however. It requires you to spend time studying the different settings you can manipulate and understanding how they work. But your not alone, many people do this, and one of the best ways to do it is to use the Arkenfox user.js project as a template. One of the benefits of tweaking Firefox is that you get to better understand what exactly your browser is doing and how it works.
The 'Arkenfox user.js' project provides a comprehensive user.js template for configuration and hardening Firefox. It is very actively maintained by some very skillful people, including an active Mozilla developer and a developer from the Tor project.
The Arkenfox user.js is very well documented, but if you feel the need for a guide I recommend you take a look at The Firefox Privacy Guide for Dummies!
Controlling Firefox's DNS over HTTPS
Mozilla has removed the option of disabling automatic updates, forcing users to get automatic updates, which if you're in the middle of some important work, will make Firefox stop opening up any new URLs until you have restarted the browser. While this exists in order to protect users, most users are quite capable of just letting Firefox remind them of an upgrade and then upgrade manually.
Because many corporations need extensive control Mozilla has created something called 'policy support' which can be implemented using a JSON file called policies.json. This file is a cross-platform compatible file that makes it the preferred method for enterprise environments to control Firefox in different environments.
By using the policies.json file you can control a great amount of how Firefox works, including the DNS over HTTPS feature.
On Arch Linux Firefox gets installed in /usr/lib/firefox/.
On FreeBSD Firefox gets installed in /usr/local/lib/firefox/.
If a subdirectory called distribution doesn't exist you need to manually create it. Then create the policies.json file in that directory.
If you should be unfortunate enough to run Microsoft Windows, the distribution directory needs to be created in the directory where Firefox is installed.
On the README for the policies templates you can find a list of options to control.
I have created a policies.json that looks like this:
You need to restart Firefox in order for the settings to take place, but if you didn't have Firefox running the settings will take place immediately. You can view your settings by typing about:policies in the address bar.
You should make sure that you have created the policies.json file before you open up Firefox for the first time after a fresh installation in order to prevent the telemetry from working the first time you use the browser.
Also notice that not all options are working on the latest version of Firefox, some only work on the ESR edition.
Last, but not least, all these options are also controllable using the user.js settings file (however, as of writing not yet all implemented in the Arkenfox version).
Blocking DoH via a firewall
No matter what kind of firewall you're running, you can at least block the known public DoH servers.
A good list with both domain names (for DNS blocking) and IP addresses (for firewall blocking) is available at: https://github.com/oneoffdallas/dohservers. Please consider making a pull request if you know something is missing.
Many other lists exist such as the one from DNSCrypt and curl.
Falkon
Falkon is a very nice browser that fully respect privacy and it is a browser that really deserves a lot more attention and a lot more support!
Falkon has been in development since 2010 and it is using the Qt WebEngine rendering engine, which is a wrapper for the Chromium browser core. The Qt WebEngine is based upon a stable version of the Chromium core with addition security fixes backported from newer versions. Prior to Falkons integration into KDE in 2017 it was known as QupZilla.
Falkon aims to be a lightweight web browser available through all major platforms and has become the default browser in OpenMandrive instead of Firefox. Falkon gives the same web standard compliance as Chromium and about the same performance, but it is more lightweight and generally starts up very fast and requires less resources. Because it uses Qt 5 it integrates extremely well with KDE, but doesn't require KDE to function as an independent browser on other platforms.
Falkon comes with a bunch of very useful build-in extensions, such as a custom ad blocker and Greasemonkey. Starting from Falkon 3.1, Falkon has gained support for custom extensions written in Python or QML which can be downloaded from the Falkon Store. As always you must be very careful with third party extensions and it is a good idea to read the source before you run any untrusted third party code in your browser or elsewhere.
I have tested Falkon and used it on a daily basis for an extended period of time and it has performed very nicely. Occasionally Falkon may choke if it enters a website that makes heavy usage of JavaScript, but I haven't experienced any crashes while using the browser. I only wish that Falkon would have a build-in extension similar to NoScript in order for the user to be able to block specific JavaScript on a per-script-basis. Instead it only has the option to enable or disable JavaScript.
Falkon has a nice set of features to secure privacy, but it must be noted that not all of these features are enabled by default. I highly recommend that you walk through the different settings before you start to use the browser.
As always it is also a very good idea to run the browser in some form of jail or sandbox, but Chromium's process isolation and sandboxing features are also enabled as a second line of defense in Falkon.
You can get in contact with developers using their mailing list and on IRC #falkon at chat.freenode.net.
qutebrowser
qutebrowser is a web browser with Vim style key bindings and a minimal GUI. qutebrowser is available through all major platforms and is included in both FreeBSD, OpenBSD and a large amount of Linux distributions.
As with Falkon, qutebrowser also uses the Qt WebEngine rendering engine, but also has the option to use Apples Webkit engine that is used in the Safari browser.
qutebrowser is based on Python and PyQt5, but because all the heavy lifting is done by the Qt WebEngine Python isn't slowing down the browser. qutebrowser loads up very fast and is very fast to use even on web pages with hundreds of links.
qutebrowser is highly configurable and the Arch Linux Wiki has a nice guide.
qutebrowser currently has a limited extensibility, but it does come with a basic support for ad blocking using a DNS styled host file. Ad blocking on YouTube doesn't work, but it is possible to configure qutebrowser to open videos links up in a media player like mpv in combination with youtube-dl, which works extremely well.
As with Falkon you need to walk through all the different settings in order to ensure that the browser is as secure and privacy-respecting as possible. DNS prefetching and a couple of other options are unfortunately enabled by default, but since the browser doesn't do anything before you ask it to, contrary to the non-privacy-respecting browser listed above, it is easy to set it up.
By typing :set you can enable a build-in GUI setup that is very well commented, and the documentation also very good.
As with Falkon and any other browser it is a very good idea to run the browser in some form of jail or sandbox, but Chromium's process isolation and sandboxing features are also enabled in qutebrowser. Security issues in qutebrowser's code happen very rarely and are fixed timely.
qutebrowser has an active development blog and a nice FAQ.
GNU IceCat
GNU IceCat is the GNU version of the Firefox ESR (Extended Support Release) browser and it is extremely privacy focused. Firefox ESR does not come with the latest features but it has the latest security and stability fixes. IceCat comes with a bunch of extensions that sometimes may brake functionality on different websites, but it is possible to control these extensions. It is also possible to disable extensions and in some cases install alternative extensions.
IceCat is one of the better replacements for Firefox, truly privacy based, and it doesn't do anything unless you actively want it to as the default settings are truly opt-in options.
Even though I have listed IceCat here as a useful alternative to Firefox, I also have very strong reservations and I do not (as of writing) recommend that you use IceCat.
The development on IceCat is active, but it is also very slow as only a small team of people is working on it. The current stable version of IceCat is based upon the 60.8 version of Firefox ESR, which has reached it's EOL (end of line at 2019-10-22) and it no longer gets any security fixes if any security bugs are found that affects that version of the browser.
The recent version of Firefox ESR is 78.4.0 (as of writing). You can still download IceCat based upon 78.4.0, but you have to download the source code and compile it yourself, and it is not considered a 'stable' release, meaning that the changes the GNU team makes to Firefox has not yet been fully implemented. Arch Linux has an AUR for the latest IceCat build for the latest version of Firefox ESR.
I have still decided to list IceCat here because it is such a good project and it deserves more support and help. Besides, most security bugs are introduced into Firefox with the development of new features, and fixed very soon afterwards, and since the ESR version don't get any new features, it is still pretty secure as is.
If you should decide to use IceCat I advice you to keep track of the development of IceCat very closely and to monitor potential security issues found in the current Firefox ESR that might also affect the old 60.x version. If a security bug is found in the current version of Firefox ESR, it doesn't automatically mean that it affects the 60.x version because it might only be related to a feature that exist in the new version. I hope that the GNU IceCat project will receive better support in the future.
ungoogled-chromium
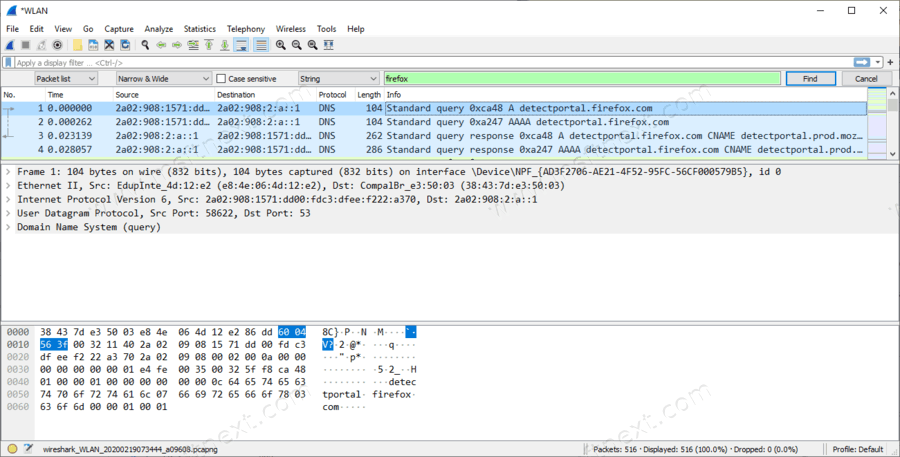
Firefox Captive Portal
ungoogled-chromium is a drop-in replacement for Chromium. It is not a diverted clone, but a set of scripts and patches that remove all background requests to any Google web services while running the browser. They also remove all uses of pre-made binaries from the source code, and replace them with user-provided alternatives when possible. They disable features that inhibit control and transparency, and add or modify features that promote them. Everything is implemented as configuration flags, patches, and custom scripts.
I have listed ungoogled-chromium here as a useful alternative to Chromium because it truly respect privacy, but I also have some strong reservations.
The team behind ungoogled-chromium is pretty small, but they do a pretty good job at tracking security updates to Chromium. However, it is very important to note that they will always be behind. Even waiting a single day or two for an update to an actively exploitable bug is critically problematic when you're dealing with the latest version of software.
However, this problem is often also the case with packages from the different Linux distributions! Distributions such as Arch Linux and Debian GNU/Linux release security fixes very fast, but other distributions are often days behind, some even weeks or months. It all depends on manpower and resources.
I don't believe that the ungoogled-chromium project should be discarded because of the small size, they are after all not cloning and making diverting changes to Chromium, they are only patching the Google stuff out of it. However, you need to closely monitor security related issues and notice how far behind the project is.
Still, another very important issue with ungoogled-chromium is that unless you compile the browser yourself, which can be very time consuming, you cannot be sure about the downloadable binaries. The binaries are provided by anyone who are willing to build and submit them. This means that authenticity cannot be guaranteed and there is always a risk that the binaries may have been tampered with!
Until the project finds a way to pre-build the binaries in a trustworthy manner I highly recommend that you only compile it yourself! I also do not recommend that you use the browser when an exploitable bug is unfixed.
Other okay browsers
Detectportal.firefox.com
These are some of the other browsers that's worth taking a look at. I haven't investigated these browsers thoroughly, but as far as I know they do not pose any problems.
- Links (console based)
- Lynx (console based)
Recommended extensions
Whether you choose to run with a tweaked or patched version of Firefox or Chromium a couple of extensions are highly recommended for both these browsers.
NoScript
NoScript is a free software extension for Mozilla Firefox, SeaMonkey, other Mozilla-based web browsers and Google Chrome/Chromium created and actively maintained by Giorgio Maone, an Italian software developer and member of the Mozilla Security Group.
NoScript allows JavaScript, Flash, and other executable content to run only from trusted domains of your choice (e.g. your banking site), thus mitigating remotely exploitable vulnerabilities, such as Spectre and Meltdown. It protects your 'trust boundaries' against cross-site scripting attacks (XSS), cross-zone DNS rebinding / CSRF attacks (router hacking), and Clickjacking attempts, thanks to its unique ClearClick technology.
uBlock Origin
uBlock Origin is a very effective open-source ad content blocker. The project specifically refuses donations at this time, and instead advises all of its clients, users and supporters to donate to block list maintainers.
uBlock Origin does get some of the ad blocking lists from websites that log IP addresses, such as GitHub, but contrary to browsers like GNOME Web or Midori, uBlock Origin only does this when you decide to upgrade the lists, it doesn't start bounching around the Internet on its own.
uBlock Origin is one of the worlds best ad blocking extensions.
Cookie AutoDelete
Cookie AutoDelete controls your cookies. When a tab or the browser closes, any cookies not being used are automatically deleted. You can prevent tracking by other cookies and add only the ones you trust and you can import and export a cookie whitelist.
HTTPS Everywhere
HTTPS Everywhere is an extension that redirects all your communications to the HTTPS version of a website. You can create a whitelist of domains if needed, such as domains running on your local servers.
Conclusions
Disable Detectportal Firefox
In my humble opinion it is absolutely mind-boggling how poor the current state of the Internet is regarding privacy issues. Almost no matter what website you visit you cannot avoid getting a microscope shoved up your ass (yes, I said it!) by some web developer who insists on running Google Analytics on the website (some even though they are not even running any Google Ads) instead of using something as simple as the build-in web server statistics, or at least one of the much better Open Source and privacy-respecting alternatives.
Detectportal Firefox Burp Suite
It is not that ads are bad in themselves. It is a fact that ads drive a huge part of the economics behind the Internet and many websites and YouTube content creators depend upon the income of ads. However, it is the way the ad business is conducted that is very problematic - in some cases even borderline immoral and highly controversial. The companies that run ad businesses need to understand that many users will actually allow ads, what users will not allow is to be spied upon and tracked without consent. These companies need to ask for permission and they need to run a completely open door policy such that all user data is transparent and available to the user. They also need to stop manipulating prices based upon tracking information, which in real life is called cheating, not business!
Anti Detect Browser Free
The Mozilla foundation is no longer the trusted organization they once were. Today it has become a 'business' that depend upon revenue from big corporations like Google, which is why we're witnessing a slow but steady move away from proper conduct. If the foundation wants to gain the trust of the users once more, they need to stop the double standard and live up to their promises.
With all that said it is important to understand that the real problem lies with us - the Internet users. We seriously need to stop using the bad browsers and we need to either stop visiting all the bad websites or at least disable JavaScript on these websites! We need to educate ourselves and others better in the technology we're using. This is much easier said than done, because website developers have gone crazy, but once you eliminate JavaScript from running in the browser you no longer need a complex browser like Firefox or Chromium and once you don't need a complex browser you no longer have to worry as much about privacy issues - at least not from the browser point of view.
Split your browsing up in between a complex browser and a simple browser. Only use the complex browser when you really need it, and use the simple browser (perhaps a console based one) when you don't require any JavaScript or other complex features.
As I said, I know that this is easier said than done, and I also know that companies will still collect as much data as possible about you (such as your IP address), but without a bad browser or JavaScript enabled the fingerprinting tactics becomes much more difficult to implement. I firmly believe that the power lies in the hands of the users and we need to make a choice every time we use technology. This is no different from boycotting harmful products because you care about yourself and your family health, or because you care about how animals are treated. We - the consumers - have the final say. When we boycott all the bad stuff, the producers have no choice but to stop the production because there are no more customers.
