This guide details how to configure Cisco ASA VPN to use the Okta RADIUS Server Agent.
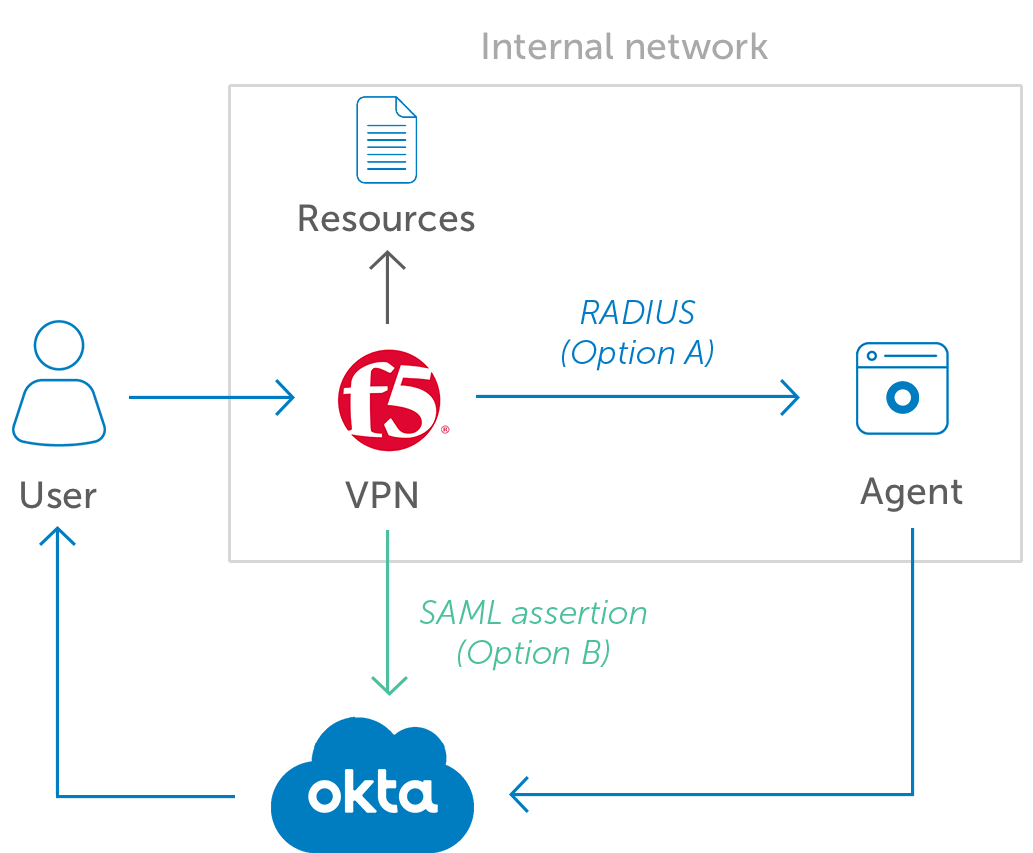
Okta and Cisco ASA interoperate through RADIUS. For each Cisco ASA appliance, you can configure AAA Server groups which can be RADIUS, TACAS+, LDAP, etc. Using RADIUS, Okta’s agent translates RADIUS authentication requests from the VPN into Okta API calls.
Okta is a security tool that provides sign-on and authentication services for LHC Group applications and services. It will help to manage logins, simplify the sign-on process, and make our systems more secure. You will need to register yourself in Okta to ensure you can access and login to the IT services you use. Okta is the identity provider for the internet. Learn about who we are and what we stand for. MFA for Cisco VPN Discover how Okta provides secure access to your Cisco VPNs with MFA. Configure Cisco Meraki to interoperate with Okta via RADIUS. This guide details how to configure Cisco Meraki wireless access points to use the Okta RADIUS Server Agent and EAP-TTLS. The following network diagram shows the flow between Meraki and several endpoints using Okta.
- Okta and Cisco ASA interoperate through RADIUS. For each Cisco ASA appliance, you can configure AAA Server groups which can be RADIUS, TACAS+, LDAP, etc. Using RADIUS, Okta’s agent translates RADIUS authentication requests from the VPN into Okta API calls.
- This is a bit of a complicated question. My current setup is a cisco 5515x with anyconnect partialy configured on it. Authentication is running through Okta RADIUS on a windows server.
Topics
- Before you begin
Before you begin
Before installing the Okta RADIUS Agent ensure that you have met these minimum requirements for network connectivity: Controllers for mac computers.
| Source | Destination | Port/Protocol | Description |
|---|---|---|---|
| Okta RADIUS Agent | Okta Identity Cloud | TCP/443 HTTP | Configuration and authentication traffic |
| Client Gateway | Okta RADIUS Agent | UDP/1812RADIUS(Default, may be changed in RADIUS app install and configuration) | RADIUS traffic between the gateway (client) and the RADIUS Agent (server) |
Supported factors
The following MFA Factors are supported:
When integrating with Okta RADIUS, the maximum supported number of enrolled factors is dependent on the size of resulting challenge message. Okta recommends that no more than eight ( 8 ) factor be enrolled at one time.
| MFA Factor | Password Authentication Protocol PAP | Extensible Authentication Protocol - Generic Token Card EAP-GTC | Extensible Authentication Protocol - Tunneled Transport Layer Security EAP-TTLS |
|---|---|---|---|
| Custom TOTP Authentication | Supported | Supported | Supported |
| Duo(Push, SMS and Passcode only) | Supported | Not supported | Not supported |
Supported | Supported | Not supported | |
| Google Authenticator | Supported | Supported | Supported - as long as challenge is avoided. For example MFA only or password, MFA. |
| Supported | Supported | Supported - as long as challenge is avoided. For example: MFA-only or password, MFA for TOTP. Push can work with primary auth + MFA as the push challenge is sent out-of-band. | |
Supported | Supported | Supported | |
| Supported | Supported | Not supported | |
| SMS authentication | Supported | Supported | Not supported |
| Symantec VIP | Supported | Supported | Supported |
| Supported | Supported | Not supported | |
| Supported | Supported | Supported |
Note
The U2F Security and Windows Hello MFA factors are not compatible with RADIUS-enabled implementations. Blood allison moorer.
For additional information about the RADIUS apps refer to Configuring RADIUS applications in Okta.
Typical workflow
Task | Description |
|---|---|
| Download the RADIUS agent |
|
| Install the Okta RADIUS Agent. |
|
| Configure application |
|
| Configure gateway |
|
| Configure optional settings |
|
| Test |
|
Cisco Anyconnect Mfa Options
Related topics
Cisco Anyconnect Okta
- Current Cisco ASA and ADSM Configuration Guides: https://www.cisco.com/c/en/us/support/security/asa-5500-series-next-generation-firewalls/products-installation-and-configuration-guides-list.htm
- Installing the Okta RADIUS Agent under Windows or Linux.

